Hey, you! Happy Tech Thursday! Thanks for joining me for this special lesson and a wake-up call about how cl ose cybersecurity affects each and every one of us.
ose cybersecurity affects each and every one of us.
“Please put that away!!” I hear towards the end of 8th period World History on Wednesday. I’m in the middle of a worksheet and I hear the student respond, “But this is important! I got an email…it’s from the school…it says that there’s been phishing…with a ‘p-h’…emails!” I instantly look up, subconsciously catching this phrase and instantly feelings the reality, the sour, the hard-hitting reality, hit me about my project. That the problem is in our backyard. That the threats are only getting worse. That EDUCATION and AWARENESS is becoming increasingly imminent as a digital native!
After school, I checked my school email:
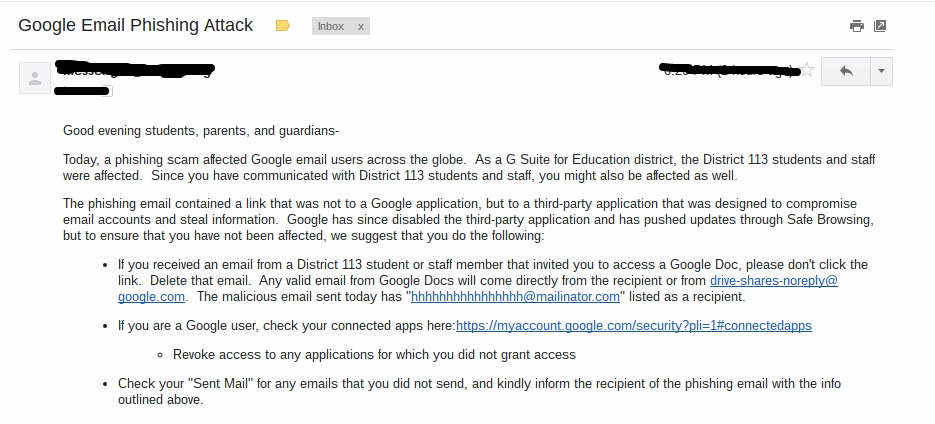

Sure enough! Although I was not personally affected, it opened my eyes and the eyes of my fellow peers that these issues begin right at school! The safety of institutions and even our government begins with personal security. In fact, 90% of the time a system gets hacked, it’s because of a SIMPLE mistake made by human error! Actually, this particular phishing attack made it on the news as a massive attack on Google Docs, one of the largest data warehouses and cloud computing storage hub. Exploiting the data from accounts and documents could leak MASSIVE amounts of sensitive information about students, teams, businesses, and personal pro
files! Check out more about the specific hack on NBC here!
For this reason, and much more, I wanted to turn this pervasive event into a learning opportunity. provide some tips on how to protect yourself and what to always keep an eye out for. Let me break it down:
What is it? A phish is an email, IM, or message from a “reputable” entity such as a bank, school, company [although it is really a hacker]… that asks for the user to download a document, open a document, or click on a link- all in order to compromise sensitive information from the atack-ee. Hackers today are automated, using sophisticated algorithms to send mass emails to targets and try all weak links.
Who is behind it? Hackers or hacking organizations [obviously NOT the company sending the message] who can use your password, credit card, and usernames for identity theft or to sell it for money on the cyber-criminal black market. If the scam is planned out, the attack could be to take down the infrastructure of a company or organization.
Why would I fall for it? These emails look real! Hackers are getting more sophisticated with their emails, links, and sign-in pages that make it seem like a real situation. In the midst of our busy lives, we fall for these tricks. BUT NOT ANYMORE, I TELL YOU!
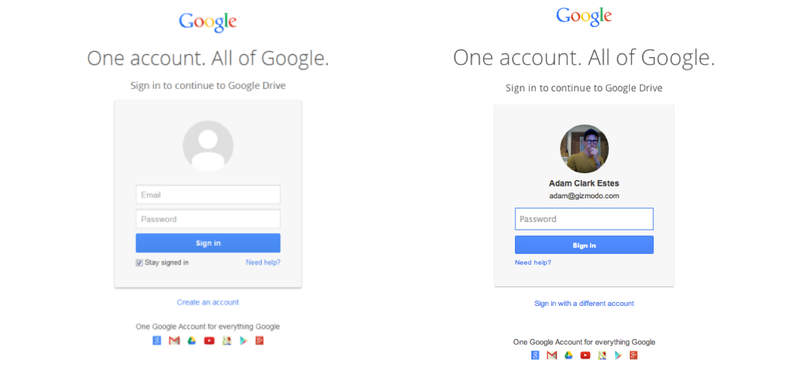
Which one is real? Source: Gizmodo
Answer: Neither! These are the screens you would see if you clicked on the link. The data you fill out does NOT go to Google’s server as it would, it is directed to a hacker’s terminal.
What data are they getting? Passwords, usernames, credit card numbers, computer search history (through malware inserted), the malware they insert really has several capabilities like tracking keystrokes, tracking server traffic, and even turning your computer into a bot! Point is, the data we store on these services is SO MUCH more than we can see, and we can really pull this apart as we look as privacy policies. These services are free, but at the cost of A LOT of data. We need to help keep this data in the right hands.
What happens if I click the link? Dying to know? Don’t press it! I’ll let you in on the secret: It takes you to a log-in screen that is CON-VIN-CING! You unknowingly fill it all out and BAM! That data is collected by the malicious party. A lot of times, these links contain malware that is also downloaded onto your device which you can check out and learn all about RIGHT HERE!
How can I tell?
- The more urgent the email sounds, the more risky it is to download or click.
- Were you expecting an email from your senior manager today with this document? Send them a quick email or ask around to find out!
- Spelling errors are also a common key in detecting a spam email.
- If there is a general opening, like Dear Valued Customer…
- Unknown Sender
- Garbled or email that does NOT correspond to the organization they supposedly represent.
- Has an attached download or file–> If it is expected, run a scanning software on the file before downloading to check
- Does not sound like the sender
- The FROM name, ADDRESS field, REPLY TO are seemingly the names of the executives being impersonated, but the reply-to’s address is the hacker’s.
- CFO, Finance, HR are all commonly email attack topics/imposter vunerabilities.
- Vague subject line (Documents, Download)
Source: Proofprint
What do I do if I get one?
DELETE it! Do not click or forward it! Send it to spam, spread the word on a shared base with your organization and let people know that this has happened. Since this is automated now, it is likely that this is all over the office! Reset you password, install anti-malware (if you do not have this already), check out these anti-phishing scam blocker resources, and become a stronger, more experienced digital user.
A general rule: NEVER instantly trust the sender of any email, even if it is from a mom, dad, brother, friend, or coworker unless you have justified, rational reasons to do so.
Reflection Questions: How would you react to a phishing attack? Have you been affected, do you know of anyone who has? What can you do to prevent phishing attacks? What are the most telling signs of one?
It’s all a part of living a digi-centric life, something that we have to deal with everyday and should be prepared to deal with at any time. Today, I was told that culture starts at home and continues through school. As we have seen, even in my district, this is the second massive, publicized identity theft crisis that has happened in two school years, and highlights the importance of knowing the cost/risk/prevention. s
Thanks for joining me this week! As always, stay safe and be active, engaged, and always watchful digital citizens.
Detective Safety


