Hey there, you!
Thanks for joining me this week on Bits N’ Bytes for a quick guide to the different types of malware! (Yes, there is a variety of malicious software & truly enough to make our heads spin)
Why is this important? Much too often, businesses or individuals do not patch their operating systems and the software on phones, PCs, and devices. Without patching, we leave holes and vulnerabilities that make it easy for hackers to gain access to our data. In order to completely understand and be able to mitigate issues on our devices, we need to be able to recognize the type of attack. Here’s the most wanted list for malware:
Malware: Malicious Software that can cause harm to your computer. Sometimes, we are not able to see the malware on our device causing harm tangibly, but other times we can. Malware can steal data, compromise function, and damage the host device.
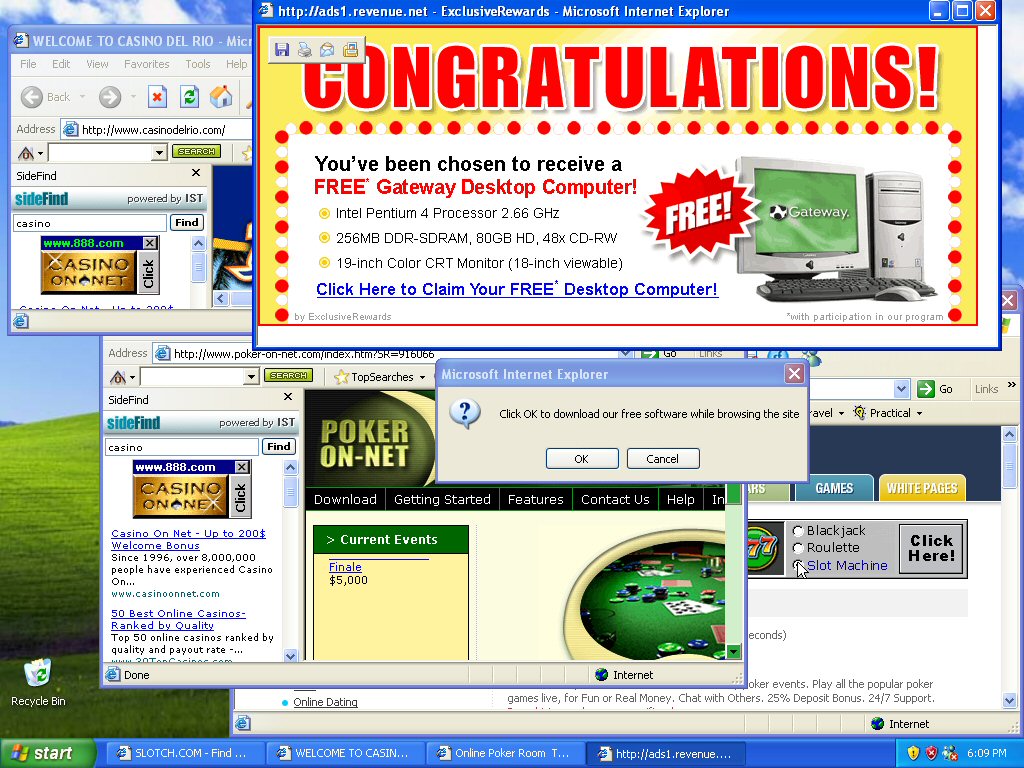
Adware Examples: Overwhelming, but awfully common! Source: MHS AoIT
1. Adware: Advertising Supported Software- Software that delivers “inviting”
ads that are installed by companies for revenue. Adware is seen everywhere, you’ve probably seen it pop up tons of times on your screen. Although sometimes they are solely for advertising, when criminals bundle adware with spyware(TBDiscussed), the two reckless pals can track user activity and steal information. How can you tell which adware is alone and which is bundled? That’s the catch- there’s no way to know.
 2. Bots- “robot network” Programs that are literally “programmed” to do certain tasks on your computer. Some are harmless like those used in video games and online contests. However, bots can be used maliciously. For example, the mass use of bots to create “botnets” or “armies” of bots allow hackers to DDoS servers of institutions. To DDoS means to overwhelm and crash the server by sending too many requests at once (used maliciously). You know those CAPTCHA tests you have to fill out when you register for something? Those are to protect against “bots” that try to infiltrate systems. A Botnet is a large, distributed army of automated computers that can be controlled by one central power to execute large-scale DDoS Attacks.
2. Bots- “robot network” Programs that are literally “programmed” to do certain tasks on your computer. Some are harmless like those used in video games and online contests. However, bots can be used maliciously. For example, the mass use of bots to create “botnets” or “armies” of bots allow hackers to DDoS servers of institutions. To DDoS means to overwhelm and crash the server by sending too many requests at once (used maliciously). You know those CAPTCHA tests you have to fill out when you register for something? Those are to protect against “bots” that try to infiltrate systems. A Botnet is a large, distributed army of automated computers that can be controlled by one central power to execute large-scale DDoS Attacks.
 3. Bugs- If you code, you know what a “bug” in your program means. It’s simply an error in your program that is either a logic(behind-the-scenes) or a syntax error(visible). Some bugs are relatively harmless, however other
3. Bugs- If you code, you know what a “bug” in your program means. It’s simply an error in your program that is either a logic(behind-the-scenes) or a syntax error(visible). Some bugs are relatively harmless, however other
s crash and freeze devices. Security bugs are the worst mistakes as they allow hackers to bypass authentification, gain access, or steal confidential business data. How can this be avoided? Simply by quality control, educating the developer, and using analysis tools.
4. Ransomware- As we discussed previously, this type of malware holds data for ransom. It forces the user to pay to regain access and gets onto a device through a malicious download or another vulnerability in the network.

The camouflage malware! Source: Phys
5. Rootkit- Malware that gains remote access without being detected by users or security measures. The rootkit can operate in a hidden way and can execute files, modify configurations, or alter security software WITHOUT BEING CAUGHT! It modifies the operating system and can only be detected by more manual methods such as storage dump analysis and observation of irregular activity. Be an active user!
5.  Spyware- Can spy on user activity on a device like keystrokes(keylogger) and user credentials. Spreads by exploiting software vulnerabilities(bugs) or bundling itself with other types of malware like adware or trojans(TBDiscussed). Typically used to gain intelligence on the victim, party, or organization.
Spyware- Can spy on user activity on a device like keystrokes(keylogger) and user credentials. Spreads by exploiting software vulnerabilities(bugs) or bundling itself with other types of malware like adware or trojans(TBDiscussed). Typically used to gain intelligence on the victim, party, or organization.
- Keylogger: Secretly records user keystrokes.
6. Trojan Horse- Disguises itself as a normal file, hiding in a genuine application. Tricks the user into authorizing it’s download or clicking on it. Once it is downloaded, the software can steal credentials, use the computer as a botnet, or monitor user activity. An Example would be Hummer, an Android Trojan that gained root privileges, installing unwanted games and applications onto mobile devices.
7. Viruses: Known for replicating itself and spreading to other computers or programs. Executes when the user opens the infected program like a file or document. Viruses can be used to create botnets, harm the host, and steal money or data.
8. Worms- One of the most common types of malware, exploiting system vulnerabilities. (Type of virus) They spread rampantly over networks. Commonly contain “payloads” which are packets of code intended for specific damage targeting the system like gathering data or deleting data. The major difference between worms and viruses are that you do not have to click on a malicious link or download a spurious document for worms to spread. However, they usually spread through mass email spam. 
9. Spam: Most commonly seen on email but also on instant messaging, texting, blogging, and soci
al media. Happens are a result of other worms or types of malware affecting your device. AVOID unfamiliar messages and keep your email address(And all your personal information) as private as can be!
Many of the common types of malware overlap, but each contain their own unique damaging and dangerous qualities. These criminal critters may not seem common and threating, as we tend to think that we have nothing on our devices that are worth stealing. However, everyone is vulnerable, and every device is vulnerable. So how can we protect ourselves?
-
Know the symptoms:
-
Slow computer or browser
-
Problems connecting
-
Freezing or crashing
-
Modified or deleted files without your authorization
-
Appearance of strange files, programs, or desktop icons
-
Programs running, turning off, or reconfiguring themselves (malware will often reconfigure or turn off antivirus and firewall programs)
-
Strange computer behavior
-
Emails/messages being sent automatically and without user’s knowledge (a friend receives a strange email from you that you did not send)
-
- RUN AND INSTALL ANTI-MALWARE!! Make sure you select an anti-malware, not just anti-virus, that detects, quarantines, and removes all or most of the malwares discussed above! Know that you know that there is much variety, we know there is a lot to protect against!
- Keep software up to date with constant updates and patches! Always do it as soon as possible. It may seem like a hassle, but we learned how many types of malware rely on unpatched bugs and holes!
- Be on the lookout for malicious or suspicious downloads, files, and attachments.
- Share these tips with those around you! Data is like a precious stone we need to safeguard and protect.
Thanks for joining me this week!
As always, stay safe & be a safe-digital leader!
Detective Safety
Source:
“Common Malware Types: Cybersecurity 101.” Veracode. N.p., 04 Feb. 2016. Web. 30 Mar. 2017.


